
Black Box Testing
In penetration testing, black-box testing refers to a method where a penetration tester has no knowledge of the system being attacked. The goal of a black-box penetration test is to simulate an external hacking or cyber warfare attack.
Specific knowledge of the application's code, internal structure and programming knowledge in general is not required. The tester is aware of what the software is supposed to do but is not aware of how it does it.
Sometimes coined a "zero knowledge penetration test".
No authentication is presented to the penetration tester.
Gray Box Testing
A black-box tester is unaware of the internal structure of the application to be tested, while a white-box tester has access to the internal structure of the application. A gray-box tester partially knows the internal structure, which includes access to the documentation of internal data structures as well as the algorithms used.
Gray-box testers require both high-level and detailed documents describing the application, which they collect in order to define test cases.
Authentication is granted to the penetration tester.
White Box Testing
White-box testing is a method of software testing that tests internal structures or workings of an application, as opposed to its functionality (i.e. black-box testing). In white-box testing an internal perspective of the system, as well as programming skills, are used to design test cases.
These different techniques exercise every visible path of the source code to minimize errors and create an error-free environment. The whole point of white-box testing is the ability to know which line of the code is being executed and being able to identify what the correct output should be.
Full access to the penetration tester including source code.
Penetration Testing Services Overview
Steps to Schedule Your Penetration Test:
- Schedule a pre discovery session.
- We determine how we can help you.
- We provide a tailored proposal.
- Together, we review the proposal
Our service highlights
- CISSP - Certified Information Systems Security Professional.
- OSCP - Offensive Security Certified Professional.
- OSWE - Offensive Security Web Expert.
- OSCE - Offensive Security Certified Expert.
- OSWP - Offensive Security Wireless Professional.
- CRTE - Certified Red Team Expert.
- CRTP - Certified Red Team Professional.
- CDNA - Certified Network Defence Architect.
- CCP - AWS Certified Cloud Practitioner.
- CEH - Certified Ethical Hacker.
- Proven methodology.
- Stellar remediation path.
- Clear and concise reporting.
- Letter of attestation.
- Extremely approachable.
Ask yourself these questions:
Why not take action now to protect your systems, your employees, and your customers from a digital attack?
A penetration test strengthens your defenses by revealing your weaknesses. Vader Security, LLC can help prioritize remediations to secure your infrastructure.
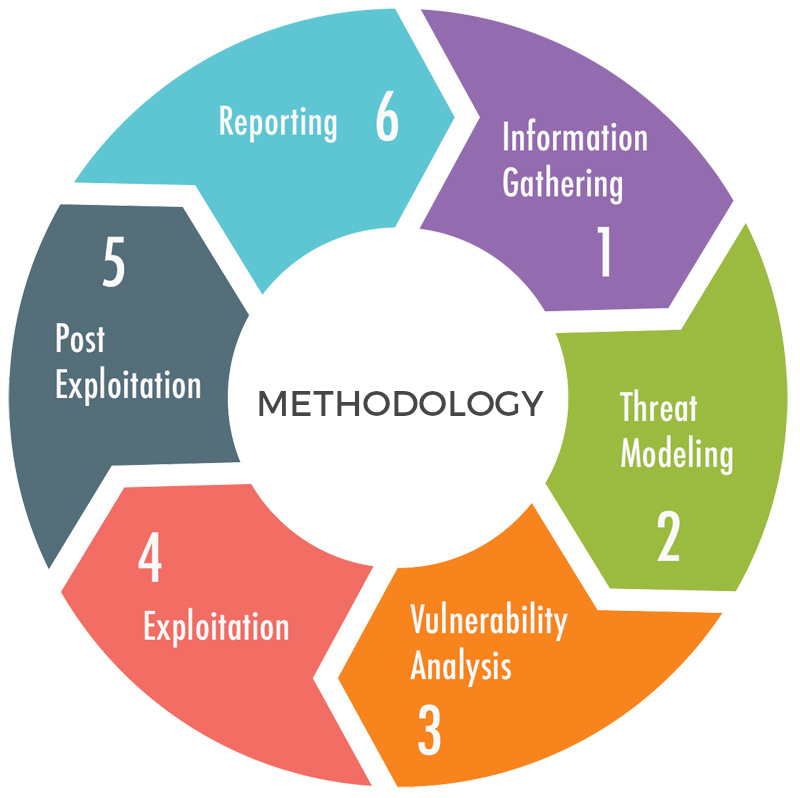
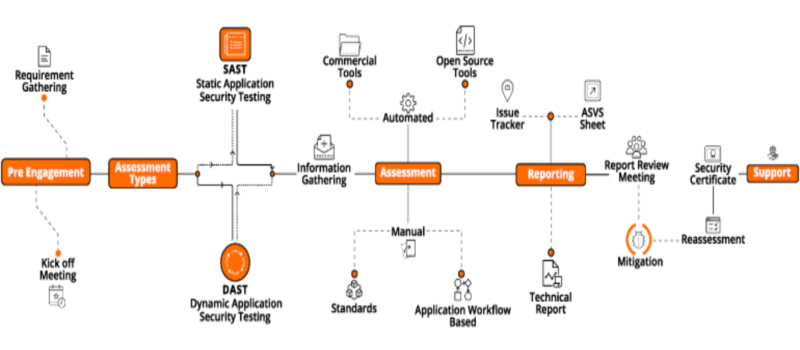
What makes us unique
We Do Not not offer any single type of penetration test.
We work with the customer to identify their needs from an attackers standpoint. From testing a single Internet address or web application to fully encompassed external and internal "red-team" style engagement. We will adjust the needs of the test to the scope requested by the customer.
We use the same tactics, techniques and proceedures a valid threat actor would use. We will attempt to infiltrate your company by all means nessassary.
Scope and terms must be agreed by both parties.